Machine Learning for Encrypted Malware Detection
ML detects malware in encrypted traffic using TLS metadata, packet sizes and timing—high accuracy without decrypting payloads.
Encryption now protects over 90% of internet traffic, but it also hides malware, making it harder to detect. Traditional methods like Deep Packet Inspection no longer work effectively because they can't analyze encrypted data. Machine learning (ML) offers a solution by analyzing patterns in metadata and traffic behavior without decrypting data. Here's what you need to know:
- Why ML Works: It identifies threats by looking at packet lengths, timing, and TLS handshake details instead of decrypting traffic.
- Key Techniques: Supervised learning (using labeled data) excels at spotting known threats, while unsupervised learning (detecting anomalies) is better for new, unknown malware.
- Performance: ML models have achieved up to 99.8% accuracy in detecting malicious traffic.
- Challenges: Handling evolving malware, imbalanced datasets, and ensuring real-time detection remain critical hurdles.
ML-based detection is shaping the future of cybersecurity by offering privacy-friendly ways to tackle encrypted threats while maintaining high accuracy.
Machine Learning for Encrypted Malware Traffic Classification
sbb-itb-f3ffd9f
Machine Learning Techniques for Encrypted Malware Detection
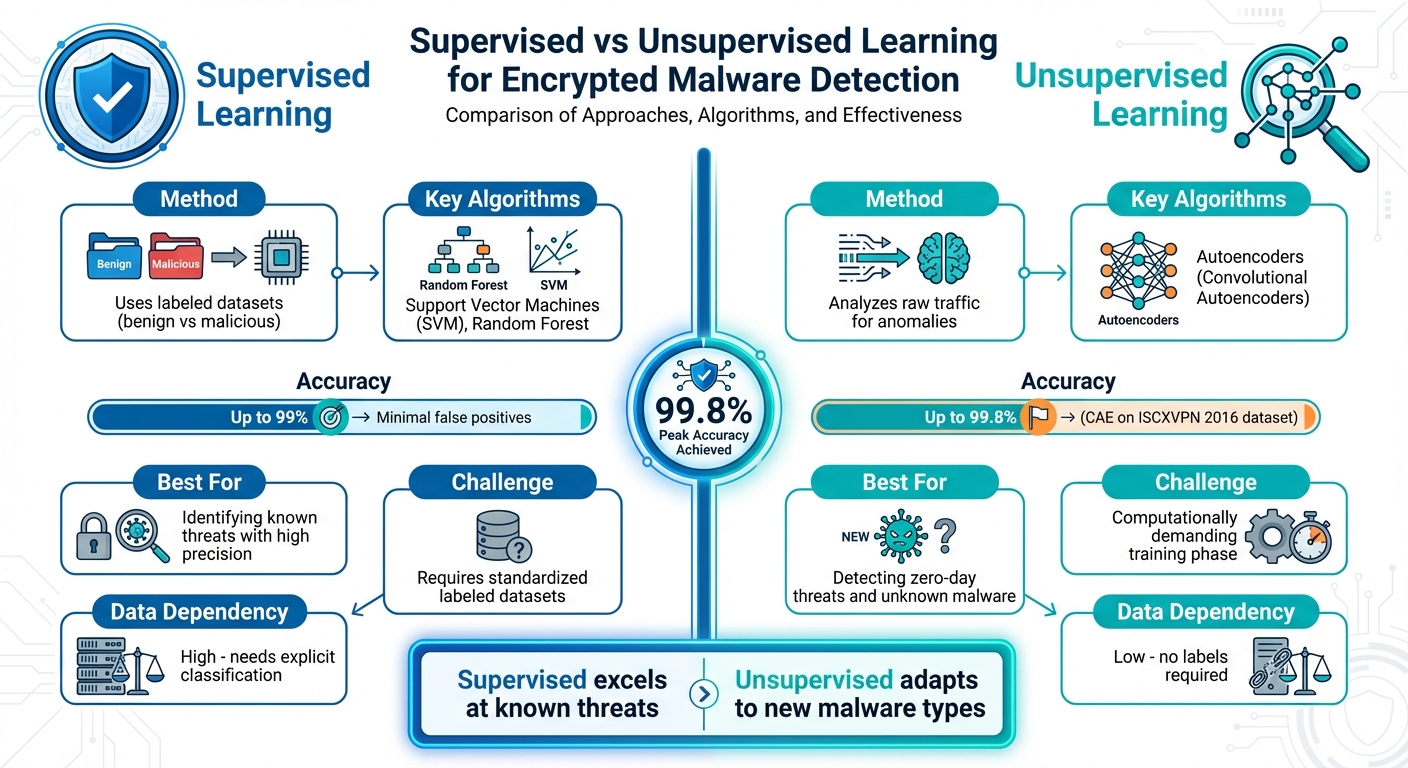
Supervised vs Unsupervised Machine Learning for Encrypted Malware Detection
Supervised vs. Unsupervised Learning
When it comes to identifying encrypted malware, two key approaches dominate: supervised learning and unsupervised learning. Each has its own strengths and challenges. Supervised learning relies on labeled datasets that explicitly classify network traffic as either benign or malicious. Algorithms like Support Vector Machines (SVM) and Random Forest use these labels to learn patterns and make predictions for new traffic. However, a major hurdle in this method is the lack of standardized datasets, often requiring researchers to piece together data from various sources.
Unsupervised learning, on the other hand, doesn’t depend on labeled data. Instead, it uses techniques like Autoencoders to analyze raw traffic and detect anomalies - patterns that deviate from the norm. This makes unsupervised learning particularly effective for identifying "zero-day" threats, which are unknown attacks that haven’t been encountered before. While supervised learning tends to excel at identifying known threats with high precision, unsupervised methods offer the flexibility to adapt to new and unforeseen malware types.
Feature Engineering for Encrypted Traffic
Detecting malware in encrypted traffic without decrypting it requires a focus on metadata and behavioral characteristics. The process begins with data preprocessing, where raw packet data is converted from hexadecimal to decimal, and categorical elements like TCP/UDP flags are transformed into integers that machine learning models can interpret.
Some of the most important features for analysis include TLS handshake metadata (such as cipher suites, TLS versions, and extension counts), packet length sequences, and inter-arrival times between packets. Researchers also group packets using "4-tuples" (Source IP, Destination IP, Destination Port, and Protocol) to calculate metrics like average packet size and standard deviation. For example, the TLSmell framework reduced 33 initial indicators to 16 highly effective features using techniques like Fisher Score and Select K Best. This optimization led to a 1.2% improvement in accuracy for deep neural networks compared to traditional SVMs. By focusing on the most relevant features, researchers not only improve model performance but also reduce training time and computational costs, making these methods more practical for real-world applications.
Case Study: Support Vector Machines and Autoencoders
Support Vector Machines have demonstrated impressive results, achieving up to 99% accuracy with minimal false positives. Research by Michael J. de Lucia and Chase Cotton, published by IEEE, highlighted SVM's superiority over Convolutional Neural Networks (CNNs) across all evaluation metrics. As they stated:
"The SVM method outperforms the CNN method in all evaluation metrics presented".
Meanwhile, Convolutional Autoencoders (CAE) achieved even greater accuracy, reaching 99.8% on the ISCXVPN 2016 dataset. When tested against VPN-encapsulated malware, CAE outperformed CNN models, which achieved 92.92% accuracy. However, Autoencoders come with a trade-off: their training phase is computationally demanding, requiring larger datasets and more processing power. Despite this, once trained, Autoencoders are highly efficient, making them an excellent choice for real-time applications where speed is critical.
Recent Frameworks and Methodologies
MH-Net: Multi-View Heterogeneous Graph Model
Recent advancements in machine learning have introduced groundbreaking approaches to encrypted malware detection, with MH-Net (Multi-View Heterogeneous Graph Model) leading the charge. First presented in 2025, MH-Net takes raw traffic data and breaks it into 4-bit or 8-bit units, creating multi-view graphs. Its standout feature is the use of Point-wise Mutual Information (PMI), which captures fine-grained correlations in encrypted traffic. By focusing on relationships like header-header, header-payload, and payload-payload, MH-Net identifies malicious patterns without the need for decryption, offering a more nuanced and secure detection method.
MIETT complements this by employing a multi-instance approach with two-level attention (TLA) layers, which analyze token- and packet-level relationships. This design achieves exceptional results in encrypted traffic classification, effectively identifying complex threats that could evade simpler detection systems.
CNN and XGBoost for HTTPS Traffic Classification
Beyond graph-based models, deep learning and ensemble techniques are pushing boundaries in HTTPS traffic classification. Convolutional Neural Networks (CNNs) have shown impressive results, with a single CNN model achieving 99.34% accuracy and a ROC-AUC of 99.99% on a dataset of 145,671 HTTPS flows across six categories: Download, Live Video, Music, Player, Upload, and Website. A stacked ensemble meta-learner combining multiple models further boosted performance, reaching 99.49% accuracy and a Macro-F1 score of 99.32%. Improved CNN architectures have also enhanced detection accuracy by 7.61% and recall by 8.23%, reducing missed threats and strengthening security in real-world applications.
Performance Comparisons Across Techniques
Frameworks like SmartDetector are reshaping the detection landscape by using contrastive learning to derive deep representations from unlabeled data. Even under evasion attacks, SmartDetector maintained F1 scores and AUC values above 93%. Multi-task learning frameworks have also delivered impressive results, achieving 99.29% accuracy for encapsulation detection and 96.89% for application identification using the ISCX 2016 dataset. These frameworks excel by sharing representations across related tasks, improving both accuracy and computational efficiency. Compared to traditional models like SVM or Random Forest, deep learning methods have demonstrated improvements of up to 86% in F1-score and 64% in precision in complex encrypted environments.
| Metric | Purpose | High-Performance Benchmark |
|---|---|---|
| Accuracy | Percentage of correctly classified samples | 95% – 99.5% |
| Precision | Fraction of true positives among predicted positives | 0.96 – 0.99 |
| Recall | Percentage of actual positives correctly identified | 0.94 – 0.99 |
| F1-Score | Harmonic mean of precision and recall | 0.95 – 0.99 |
| ROC-AUC | Ability to distinguish between classes | 0.999+ |
Challenges and Future Directions
Handling Non-Stationary and Imbalanced Data
Even with advanced machine learning (ML) methods making strides in encrypted traffic analysis, some hurdles remain - especially when it comes to handling data variability and real-time applications. One major issue is how ML models struggle to keep up with the constantly evolving tactics of malware. Attackers are always updating their encryption methods and tweaking their code, creating non-stationary data that can quickly render existing models ineffective.
Take frameworks like RAPIER, for example. This system has been designed to deal with non-stationary data and high levels of label noise - up to 45% - while still achieving F1 scores between 0.770 and 0.855 on enterprise-level datasets. It works by observing a key pattern: normal traffic tends to cluster tightly in feature space, while malicious traffic is more scattered. This distinction is used to improve training data and correct mislabeling.
In scenarios where data is imbalanced, ensemble methods like XGBoost and Random Forest have shown exceptional results, achieving precision rates as high as 99.78% and false detection rates below 0.5%. Another standout innovation is the SmartDetector framework, introduced in April 2025. Using contrastive learning, it extracts deep representations from unlabeled data and maintains F1 scores and AUC values above 93%, even during evasion attacks. This represents an average improvement of 19.84% over older methods. These advancements underline the pressing need for ML models to be seamlessly integrated into real-time systems.
Real-Time Detection Integration
Speed is a critical factor when deploying ML models in production environments. While deep learning models like LSTMs can achieve impressive accuracies of up to 99.5%, their high computational demands can make real-time processing a challenge - especially given the rapid pace of network traffic.
"Fixed feature methods may be bypassed by deliberate obfuscation." – Ke Ye, Institute of Computer Application
Organizations face a tough balancing act: how to maintain high detection precision without sacrificing processing speed. One promising solution emerged in July 2025 with the development of RobustDetector (RD) by researchers at the China Academy of Engineering Physics. This system uses a dual-CNN architecture with dropout layers to simulate evasion attacks during training. When tested on the CICIDS2017 dataset, it achieved a 90.63% F1 score - even when traffic was deliberately obfuscated with random delays and artificial packets. Additionally, session-based grouping, which organizes packets by source IP, destination IP, and session time, has proven effective in capturing temporal patterns more efficiently.
Future Research Directions
To tackle these challenges, Automated Machine Learning (AutoML) is gaining momentum. AutoML simplifies the complexity of encrypted traffic analysis by automating tasks like hyper-parameter tuning and feature selection, reducing the need for deep expertise. This makes it easier for organizations to adopt and deploy ML systems.
Another critical area of focus is privacy-preserving detection. By late 2023, around 91.5% of malware was being delivered over encrypted connections, and this figure is expected to grow with the adoption of protocols like TLS 1.3 and HTTP/3. Future detection systems must find ways to identify threats without decrypting payloads, preserving the privacy benefits of encryption while still identifying malicious activity. Federated learning is also gaining attention, allowing multiple organizations to collaboratively train models without sharing sensitive traffic data - a promising approach for industries dealing with strict data regulations.
Lastly, there’s the issue of interpretability. Deep learning models often operate as "black boxes", leaving security teams in the dark about why certain traffic is flagged as malicious. To address this, future research should prioritize developing explainable AI systems that security analysts can understand, trust, and validate.
Conclusion
By the end of 2018, 72% of internet traffic was encrypted. Fast forward to 2023, and a staggering 91.5% of malware was found to use encrypted channels. This shift has made traditional security measures less effective, as they often rely on analyzing unencrypted payloads. Enter machine learning: a game-changer that focuses on traffic behavior and metadata instead of decrypting sensitive data. By analyzing elements like packet timing, TLS handshake details, and connection patterns, these systems detect malicious activity without infringing on user privacy.
As Zihao Wang and colleagues note in Computers & Security:
"Machine learning based approaches have become an important direction for encrypted malicious traffic detection" as "common security solutions that rely on plain payload content analysis... are rendered useless."
For businesses, these advancements bring both opportunities and challenges. While ML-based detection offers a powerful way to combat encrypted threats, many U.S. enterprises struggle with the complexities of feature engineering, model tuning, and real-time deployment. This is where industry leaders step in to simplify these processes. Companies like Integrity Tech provide tailored cybersecurity solutions, integrating ML-driven threat detection to offer robust protection without burdening businesses with technical intricacies.
Looking ahead, the future of cybersecurity will hinge on behavioral analysis, automated machine learning, and privacy-preserving detection techniques. By leveraging these tools, organizations can stay one step ahead in the ever-evolving battle against cyber threats.
FAQs
How can machine learning identify malware in encrypted traffic without decrypting it?
Machine learning offers a smart way to detect malware in encrypted traffic without the need to decrypt it. Instead of breaking the encryption, it focuses on analyzing observable patterns and metadata. These include packet sizes, timing between packets, traffic flow statistics, and information from the TLS handshake. By training algorithms to identify unusual or suspicious behaviors in these features, machine learning models can pinpoint potential threats.
What makes this approach stand out is its ability to strengthen cybersecurity while keeping data privacy intact. It’s a powerful method for tackling today’s cyber threats without compromising sensitive information.
How do supervised and unsupervised learning differ in detecting malware in encrypted traffic?
Supervised learning depends on labeled data, where the system is trained using predefined examples to differentiate between malicious and benign traffic. This method is excellent for building precise models to detect threats that are already known.
Unsupervised learning, in contrast, doesn't require labeled data. Instead, it focuses on spotting patterns, anomalies, or clusters in encrypted traffic to highlight potentially suspicious behavior. Techniques like clustering and autoencoders are frequently employed to identify malware that is either new or evolving.
Both approaches are essential in cybersecurity. Supervised learning shines when it comes to recognizing established threats, while unsupervised learning is particularly useful for detecting emerging or previously unknown risks.
What are the main challenges machine learning faces in detecting malware in real-time?
Machine learning models designed for real-time malware detection face a host of challenges, especially when dealing with encrypted or obfuscated traffic. Encryption adds a layer of complexity, making it nearly impossible to directly analyze the data. Meanwhile, obfuscation techniques cleverly mask malicious behavior, making it harder to identify threats. Add to this the challenge of polymorphic and fast-changing malware, which constantly alters its code to evade detection, and the task becomes even more daunting.
Another significant issue is imbalanced training data. When benign data far outweighs malicious samples, models can become biased, often misclassifying threats. On top of that, high false-positive rates can inundate security teams, flagging harmless activities as potential threats and wasting valuable time.
There’s also the matter of scalability and latency. Processing massive amounts of network traffic in real time can strain resources, making it tough to maintain speed and efficiency. And as if that weren’t enough, adversarial attacks pose a serious threat. These deliberate attempts to manipulate or corrupt machine learning models can compromise their reliability and effectiveness, leaving systems vulnerable.
Related Blog Posts
Related Blogs
Ready to Transform
Your Customer Management?
Sign up today and see the difference Syncro can make for your business.


.svg)